In the United States, about 19% of the adult population has experienced identity theft. Over 60 million Americans have had their online identity exposed by hacks of the customer databases of their service providers or government agencies. The situation is similar in Europe and other countries.
Identity theft is not the only crime that walks hand in hand with hacked passwords and compromised online accounts: credit card fraud, blackmail, privacy invasion and illegal wiretapping all occur frequently throughout the world.
Multi-factor authentication (MFA, sometimes simplified as ‘two-factor’ or 2FA) has been proven to be an effective tool for enhancing the security of online accounts. However, enabling MFA or 2FA does not mean your account is automatically secure.
The military and elite have used MFA for centuries. For example, in the Three Musketeers by Alexandre Dumas, d’Artagnan receives a ring from Queen Anne of France in addition to the spoken instructions he needs to use to communicate to the Duke of Buckingham in order to warn the Duke that Cardinal Richelieu and Milady de Winter are plotting to kill him.
The modern use of MFA for securing computer records and online accounts originated in the banking sector, the typical example being cash withdrawal from an ATM, which requires having a banking card and knowing your PIN.

Person using ATM. Image by Pixabay
In the early 2000s, banks, online stores and services introduced a telecom version of 2FA based on SMS containing a one-time password (OTP). Now this is synonymous with 2FA itself.
Recently, mobile applications (e.g. cross-platform Google Authenticator) brought have carrier-independent 2FA to mobile platforms using TOTP and HMAC software algorithms.
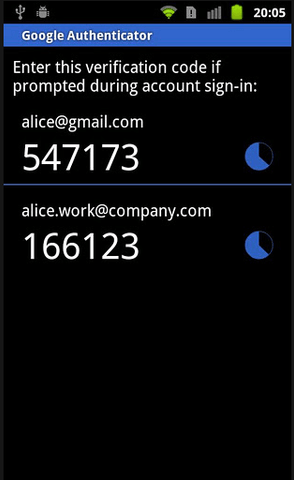
Screenshot of Google Authenticator on Android Smartphone. Image by AskUbuntu via StackExchange
So, why still bother with old-school hardware authentication tokens that require carrying yet another object around?
In this post, we will try to explain why a hardware second factor solution is a good option and will guide you through the features of our flagship product, the Hideez Key, which makes hardware MFA an effective and easy to use solution for such cases.
An external device is a true second factor, in fact — one of the multiple factors required to feel secure in modern cyberspace
In times when online criminals and governments can bypass even two-factor authentication, trusting your second factor to the same device you want to protect is not the best solution. The well-known three pillars of two-factor authentication are what you know (i.e. password or PIN), what you have (i.e. banking card, digital token or other physical object) and what you are (i.e. biometric data like fingerprints, iris or eye veins, the manner you type on your keyboard, soundwave pattern of your voice or heartbeat, etc.).
Customers who use software-only 2FA limit themselves to only what they know, i.e. their permanent password or passphrase and a one-time password (OTP) or PIN which is… just another password in the end. This means a computer professional or criminal who somehow got control over your client device or has the ability to see what is on your screen (think of CCTV or hidden security cameras inside modern office buildings) can bypass software-only 2FA like that.
In fact, given all the threats of the modern world, we recommend our customers to move beyond conventional 2FA to more complex MFA with biometric data as the primary factor for authentication with all other auxiliary factors required only to prove the authenticity of the confirmation message issued based on the biometric data. Here, ease of use starts to play a key role.
If setup and used properly, external devices can be more reliable than OTP
Since the late 2000s, OTPs delivered via SMS has become a very popular authentication method in banking and has spread to online services like email, social networks, cloud storage, etc. There, OTPs are easy to use. However, their reliability depends on a number of factors.
First of all, the customer needs to be sure that the mobile network used to deliver the OTP is sufficiently protected. There are publicly reports of flaws in 4G and even 5G networks already, while 3G was also compromised as early as in 2010.
Secondly, SMS OTPs are vulnerable to government wiretapping, which might be an issue for countries experiencing problems with freedom of speech and other basic human rights. Each 3G and 4G standard has mandatory instruments built in for authorized government law-enforcement agencies to access the SMS servers of mobile networks operating within the jurisdiction of the law-enforcement agency. Moreover, it is possible to intercept such SMS OTPs while the victim of an attack is using roaming in that country.
Unlike telecom operators, 2FA token hardware vendors currently have no obligation to disclose their technology to the government in most countries, as this might have adverse effects on banking security and government communications themselves. This does not mean that governments cannot target hardware 2FA technology, but the legitimate means for doing so are very limited.
Bluetooth-based external 2FA devices provide the same level of protection as a properly maintained USB hardware token, while offering the convenience of SMS-based OTP or mobile apps like Google Authenticator
While USB-based hardware tokens for 2FA are very reliable and efficient, if used properly, they require the customer to insert them into the USB slot of their device each time they need to use them. This incentivizes the customer to leave the stick ‘right in the slot’, thus making the second factor enabled by this stick vulnerable to hacking.
Hideez Key combines the reliability of a hardware second factor authenticator with the ease of use of a wireless communication protocol. The end user does not need to plug the device in anywhere, they just needs to keep it in their pocket or on a keychain close to their body.
Unlike other Bluetooth-based ‘unlock your computer’ devices, Hideez takes sniffing and MITM attacks seriously. We use additional safeguards on top of standard Bluetooth pairing. These safeguards improve the initial key exchange and make unauthorized sniffing and other signal interception techniques more difficult to perform with our devices.
The interception of Bluetooth traffic on a client device by malware might also be an issue, but we solve it by adding additional safeguards to the crypto key exchange.
How Does the Device Know its Owner?
Another critical vulnerability of any hardware second factor is the same as it is for any physical key or access token — the software assumes that the person presenting the physical token for authentication is the rightful owner. However, what if the second factor device is lost or stolen?
If a Hideez Key is lost for any reason, the user can also use My Hideez to unlink the Hideez Key from their account, or contact their system administrator. This will prevent unauthorized use of the Hideez Key.
Syncing over Bluetooth is safer than syncing via the Cloud or Wi-Fi
Knowing your password at the right moment is no less important than keeping it secure. Various mobile platforms like iCloud Keychain, LastPass, Dashlane, SafeInCloud and others offer internal and standalone password managers with cross-device synchronization features.
While all of these solutions have excellent reputations, they all use the Internet to synchronize data between the various customer devices and this means there is a potential vulnerability.
In case of a device with a local wireless connection (Bluetooth 4.2 LE in case of Hideez Key), there is no such vulnerability. End users can use our external hardware password vault as a medium for syncing passwords between various Bluetooth-enabled devices without using an Internet connection, with the associated risks. Our team mitigates sniffing and other wireless-related risks through the aforementioned additional encryption layers on the transport layer and inside the application.
Wrapping up
While software-based MFA is becoming increasingly popular and is better than nothing, the current cybersecurity environment requires truly distributed MFA. Only hardware solutions can offer this.
Still, hardware solutions must provide ease of use combined with reliability to minimize the risk that a customer might decide to take the easy option and compromise their second factor by leaving their USB stick inside their USB slot or using a ‘1111’ PIN for end user identification on the second factor device.
Bluetooth devices for MFA solve this by allowing for convenience and ease of use, while enforcing strong security practices. Notably though, they do create an additional risk of signal interception by specialized radio equipment and do not protect against the risk of data interception by malicious software, installed inside the paired device, though these types of attacks are much less common at present.
Bluetooth-based MFA solutions give customers an additional benefit of wireless syncing between the customer’s various devices without requiring the Internet.
If engineered with diligence and properly maintained by the end user, a Bluetooth-based second factor device offers ease of use and an industrial level of protection.
Learn more about Hideez Key features & specifications. If you want to implement such a solution at your company or organization - see Hideez Enterprise Solution or schedule a free demo:

