
If you’re a business owner or run an organization, no matter which scale, implementing a robust external security system is a must. The number of online threats is increasing over time, and this doesn’t only pertain to external threats. An internal security problem can have equally devastating consequences for your organization.
Plus, as remote work becomes more common in today’s corporate environment, valuable data shared in the cloud is at a bigger risk than before. Sharing documents, files, and resources with dozens or hundreds of employees means that one mistake or breach can lead to a chain of security threats. Luckily, this can all be avoided by implementing access control.
So, what is an access control system, and how can it help? On this page, we’ll discuss how access control works, its most significant benefits, and some helpful examples. Lastly, we’ll also help you secure your organization with an uncompromising access control solution.
What is Role-based Access Control? - RBAC Explained
In simple terms, RBAC is a mechanism that restricts network access for users depending on their level in the organization. It’s one of the most effective and advanced methods of access solutions. This access can be allowed based on different parameters. Most often, it’s based on authority and responsibility.
RBAC is one of the best access solutions, as it limits the risk of lower-level employees compromising valuable data. If the employee doesn’t have any responsibilities regarding a specific task, they won’t have access to the data. This makes the RBAC system excellent for organizations that regularly work with contractors, freelancers, and other third-party businesses.
How Does RBAC Work?
RBAC might sound like a complicated setup, but the truth of the matter is that the process can be separated into just several crucial aspects. Here are the three integral components of every RBAC solution:
- Identifying the users who are accessing the protected data
- Verifying that the user has permission to access the data
- Authentication and denying/granting the user access to the data.
Why Access Control is Important
Answering the question “what does RBAC stand for” and understanding how it works is just the first part of the privileged access philosophy. Arguably the more vital part is knowing why access control is so important and valuable for every organization.
In short, access control is important because it delivers a proactive approach to cybersecurity instead of a reactive one. In other words, the organization’s IT team can set up an effective system that anticipates threats and protects against unwanted intrusions. This is more efficient and cost-effective than dealing with threats as they pop up.
Given that the number of security breaches only rises with each passing year, access control is more important than ever. Cyber attacks cost businesses around the world billions of dollars, and access control is a crucial tool that can combat this unfortunate trend.
This system brings a long list of benefits to the table. The most apparent is that the organization can easily protect and monitor data and resources. This level of monitoring and control allows the organization's IT team to promptly and precisely modify access permissions for each user and quickly block specific users when necessary.
Moreover, the IT team has complete visibility over everything that goes on, as it can always know who is accessing the data, as well as when and from where they are accessing it. This is essential for any business, as most organizations don’t even have enough visibility to know who can see documents.
In line with this, the organization can efficiently onboard and offboard employees by customizing their network access permissions. The time-saving process eliminates the need for passwords and other administrative tasks. In return, the IT team has more time to focus on more important matters, such as actively improving your organization’s security.
All of this also means that the organization will have an easier task of meeting regulatory compliance requirements. This is particularly important for industries like healthcare, finance, and tech, which generally manage a lot of user data. Plus, the high level of security also acts as a great deterrent for cyber attackers who might want to steal your organization’s valuable data.
How to Implement Role-based Access?
Implementing an access control role-based system doesn’t have to be overly complex. That said, it needs to be carefully thought out and executed properly to avoid any complications or errors. Here are some tips for effectively introducing and maintaining an RBAC solution:
- Know Your Needs - The first step is outlying which employees will have which access, how this will affect your business, and whether it will have an impact on regulatory requirements. This includes writing a policy that clearly defines the principles of the new system.
- Introduce a Range - If you’re implementing RBAC and don’t have a huge budget, you don’t need to do it company-wide immediately. Consider securing data and apps that are the most sensitive and increase the scope with time.
- Implement in Stages - Rolling out a comprehensive RBAC system all at once can have a negative effect on your organization’s productivity. Instead, do it in stages and seek employee feedback to avoid any disruptions to your company.
- Make Changes and Adapt - The only way to stay ahead of the curve and maintain maximum security is to tweak and continually adapt your RBAC system. Assess your security status and access control roles regularly to keep your system as safe as possible.
Role-based Access Control Examples
To expand on the previous a bit and understand it better, let’s go over some role-based access control examples. To start with, RBAC for active directory enables your organization’s IT team to control which employee has access to what data. The team can designate whether the user has standard access and can only interact with the data or has admin access so that they can change the data or add new files.
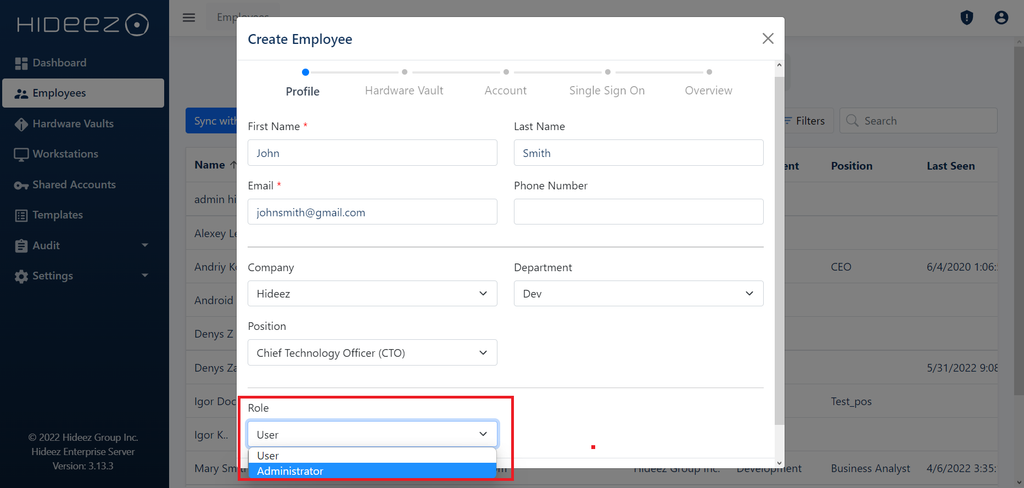
If you have a company with a few dozen employees or more, you can divide access control permissions by groups. That way, you can quickly add new users or remove former employees from a group. What’s more, this is a great way to add temporary users to a task without disrupting workflow.
For example, if you run a company that produces software, you can divide your RBAC system into groups that include software engineers, a finance group, a marketing group, an HR department, and so on. You can then further narrow this down by setting a management tier and employee tier within each group.
With precisely defined groups, each having access only to data that pertains to their side of the business, you’re minimizing the amount of data that can get compromised in case of a security breach. Following the example above, if any of the above groups suffers an external or internal problem, the other groups will be safe from any issues.
Access Control Solutions by Hideez
To sum up everything we’ve shared with you above, we first want to highlight the importance of implementing access control as a part of your IT security system. It is a valuable tool that adds a robust layer of security and minimizes your organization’s risk of a breach.
With that in mind, at Hideez, we’ve developed an advanced authentication service that enables precise control of user privileges using an RBAC system. With Hideez, you can grant users personal, shared, or restricted access to specific IT assets like web services or local password-protected files.
Additionally, our authentication system allows for efficient management of roles and permissions for employees from different departments. This is thanks to the Hideez server, which serves as a centralized virtual access control gate.
With the support of the passwordless FIDO2 standard, you can strengthen your organization’s security even further. You can do so by issuing hardware support keys to your employees or using the streamlined Hideez mobile app.
Instead of traditional passwords, your employees can lock or unlock their Windows computers based on proximity and log into web services without typing their password credentials. This entirely passwordless system enables convenient scalability and works equally well for small businesses and large corporations.
If you want to learn more about the Hideez Authentication Service, don’t hesitate to get in touch with us. You can also schedule a free demo to see how our advanced solutions can simplify and better your organization’s cyber security.

