
Cybersecurity has come a long way in the past two decades. So much so that proper identity management practices have become a basis for strong cybersecurity systems. In short, you always have to make sure that everyone is who they claim to be when requesting access. Equally as important, you should be certain that they are allowed to access what they’re requesting.
With this in mind, choosing a specific identity management approach can be challenging, especially when dealing with enterprise identity management solutions. So, to help you make sure you pick the most suitable identity management policy, we’ll cover everything you need to know about this extensive topic, all in one place.
What is Identity Management?
Identity management(IdM), also known as identity and access management (IAM) is often defined as a system used by IT departments to initiate, store, and manage user identities and access permissions. IAM includes two important processes: authentication and authorization.
In simple terms, authentication answers who you are by matching your login and password with your record in a database. Authorization checks what access and permissions you have. So, the identity and access management system is there to prevent any unauthorized access and raise alarms whenever an unauthorized user or program makes an access attempt.
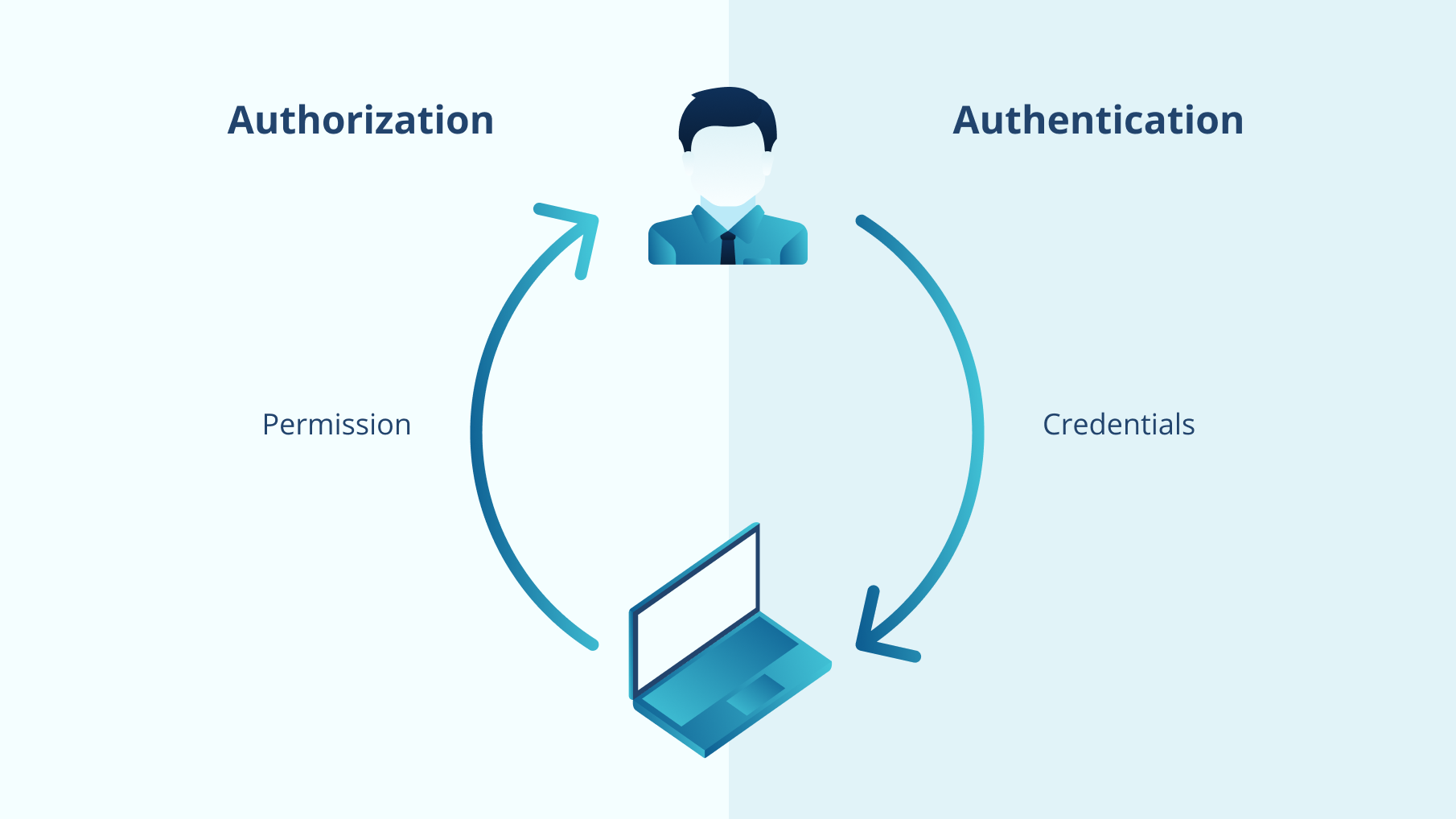
Additionally, it’s important to differentiate Identity Management and Access Management. The easiest way to do so is to remember that Identity Management is all about managing different attributes related to a user, a group of users, or any other entity that requires access. On the other hand, Access Management is about evaluating these attributes and giving a positive or negative access decision based on them.
IAM methodology ensures that users have access to the assets they need, like systems, infrastructure, software, information, but the assets are not accessible by unauthorized users. The key to secure identity management and access control lies in the combination of strong credentials, appropriate permissions, specified assets, and the right context. Identity and access management policies and procedures are developed with the principal idea in mind - prevent exposure of sensitive data.
Identity and Access Management Concepts
Identity and access management solutions, likeHideez Authentication Service, typically consist of the following fundamental elements:
- an identity repository with personal data used by the system to identify users;
- access lifecycle management tools (used to add, modify, update or delete that data);
- an access regulation system that enforces security policies and access privileges;
- a report and audit system that monitors activity in the overall system.
Identity access management tools can include automatic provisioning software, password managers, security-policy enforcement applications, monitoring apps, multi-factor authentication, single sign-on, and more.
With the advancement of technologies and an increased number of data breaches, it takes more than a strong login and password to protect an account. That’s why more and more IAM solutions use biometrics, physical tokens, machine learning, and artificial intelligence in their systems.
Identity Management Use Cases
User identity management
User identities are managed by the IAM solution. The IAM may integrate with existing directories’ identity management roles, synchronize with them, or be the one source of truth. In any case, an id management system is used to create, modify, and delete users.
User provisioning and de-provisioning
An IT department is responsible for user provisioning. They need to enter new users into the system and specify what apps, software, sites, directories, and other resources they can access.
It is essential to define what level of access (administrator, editor, viewer) every individual user has to each of them. To simplify the process, the IT department can use role-based access control (RBAC). This way, when a user is assigned one or more roles, he or she automatically gets access as defined by that role.
De-provisioning is also a critical IAM component. When done manually, it can result in delayed action and unintended disclosure. Hideez Enterprise server automates the process and immediately de-provision ex-employees.
User authentication
IAM systems authenticate a user when the user requests access. A common standard is to use multi-factor authentication to ensure stronger protection and a better ID management system overall.
User Authorization
Based on user provisioning, an IAM system authorizes user access to the requested resource if the credentials match the records in the database.
Reporting
To help companies comply with regulations, identify security risks, and improve internal processes, IAM provides reports and dashboards to monitor the situation.
Single Sign-On (SSO)
SSO is one of the best examples of modern and sophisticated identity management use cases. Only the best IAM systems like Hideez include SSO in their solution. SSO is an extra level of security that makes access for the end-user much faster, as it allows the user to use multiple resources without an additional login.
Benefits of Identity and Access Management
Enterprise identity management solutions bring about a long list of proven advantages. By implementing an access control and identity management solution, a company can gain the following identity management benefits:
- More Robust Security - Proper identity management gives companies greater control of user access and reduces the risk of a data breach. IAM systems can reliably authenticate and authorize users based on their access credentials and access levels in their directory profiles.
- Quick and Easy Access - Access is provided based on a single interpretation of the existing policy. This allows for easy access no matter where you’re trying to access from. This is a huge game-changer, as it eliminates the user’s physical location as any factor.
- Stronger and More Streamlined Internal Systems - IAM also strengthens internal policy compliance and reduces financial, labor, and time resources needed for this end.
- Increased Productivity - Automated IAM systems boost employee productivity by decreasing the effort, time, and money required to manage the IAM tasks manually. Simultaneously, this streamlined enterprise identity access management system saves on IT costs, as internal help desks won’t be as busy as before.
- Simplified Reporting and Auditing Processes - IAM assists companies in compliance with governmental regulations, as they incorporate the necessary measures and provide on-demand reports for the audit.
Identity Management for Stronger Compliance
As more attention and media exposure is given to the issue of data privacy, the government and regulatory bodies introduced multiple acts and regulations to protect client and business data. Here are the most important ones that hold companies accountable for controlling access to sensitive user information:
- PCI DSS - The Payment Card Industry Data Security Standard is a widely accepted standard for credit card companies. In the context of identity management and access management, PCI DSS can help enterprises regulate this vital financial sector.
- PSD2 - The PSD2 is a payment directive that brings great innovations into the online banking world, primarily in the form of more potent and better authentication.
- HIPAA - This is a significant identity management policy, as it established nationwide rules and standards for processing electronic healthcare transactions.
- GDPR - The General Data Protection Regulation has been in effect since 2018 and is currently one of the primary legislation pieces aiming to consolidate data protection across all EU member states.
- CPRA - The California Consumer Privacy Act is the first significant privacy law in the US that focuses on consumer control of personal data.
- Sarbanes-Oxley - The SOX identity and access management security standard applies to banking, financial services, and insurance industries.
- Gramm-Leach-Bliley - Also known as GBLA, this is a federal law that mandates that all financial institutions must maintain the confidentiality of non-public customer data. Moreover, it requires institutions to protect against threats to this information.
Identity management systems can significantly reduce the risk of breaching those regulations. Given the cost of negative audit results for the business, compliance should be a top priority for every IT department in companies subject to the before-mentioned regulations.
Enterprise Identity Management Solutions by Hideez
Choosing the right identity management products can make a world of difference in both usability and security. At Hideez Group, we’ve rolled out a new version of our acclaimed Enterprise server. It enables passwordless access with various types of FIDO authenticators. The main components of the Hideez Authentication Service are:
- Hideez Enterprise Server - A FIDO/WebAuthn server and SAML 2.0 Identity Provider. It’s a very capable server that delivers passwordless FIDO2 authentication and FIDO U2F across corporate applications and websites.
- Hideez Client Software - A streamlined application that confirms authorization and connection, and enables hotkeys for entering credentials.
- Hideez Authenticator - A mobile application that provides fast and secure access to coporate apps and web services with mobile identification. Employees can use biometric verification or scan a unique QR code to sign in to their accounts;
- Hideez Security Keys or other hardware/software authenticators - You can use your own authentication tools depending on your needs. We recommend using multifunctional security keys, the Hideez Key 3 or the Hideez Key 4 to ensure the maximum convenience and security of all end users, but you can do without them.
The Hideez enterprise identity management solution brings about a long list of benefits. It’s an all-in-one solution that enables straightforward password control without the need to disclose any credentials. It prevents phishing attacks and minimizes the risk of human error, in return ensuring better business continuity without any disruptions.
If you’re looking for reliable IAM enterprise solutions and want to go truly passwordless, get access to the Hideez Server demo version absolutely for free by contacting us right away!

