
Stolen credentials are used to commit fraud on an enormous scale through Account Takeover (ATO) or credential stuffing attacks. This presents a huge problem for businesses with employees online. Data breaches can compromise your internal documents and processes, your sensitive customer data and your financials.
Solution Overview
The user authenticates using the HTTPS web-based access to the PVWA system (the CyberArk authorization system is configured as a client of the RADIUS server). The user enters the basic credentials (Login and Password) using Hideez Key as a reliable hardware password storage. The CyberArk system, after checking and confirming the base user accounts, makes a request to the remote RADIUS server, which is configured in conjunction with the one-time password generator system, and requests the user to confirm the OTP confirmation code. The user using the Hideez Key enters a confirmation code. In case of incorrect verification of the code, access is denied to the user. Upon successful verification, the RADIUS server confirms the authenticity of the user to the CyberArk PVWA system. PVWA allows the user inside in accordance with the rights granted by the CyberArk system.
Why Hideez?
- Protects against digital identity theft, phishing, credential stuffing, and account Take-overs
- Only password keeper for digital and physical access
- Outsmart vulnerabilities of other industry players
- Increased productivity of employees
- Compatible with existing infrastructure
- Minimized risk of Human Error
Segmentation
Type: Comprises of one key password, public key infrastructure and others.
Model: Comprises of smart card with pin, smart card with biometric technology, biometric technology with pin, two-factor biometric technology, one-time password with pin and others.
Technology: Comprises of physical and logical access control, SafeNet OTP authenticators, out-of-band authenticators, Mobile PKI office suite, PKI authenticators and others.
End User: Comprises of banking and finance, consumer electronics, healthcare, government, travel and immigration, military and defense, commercial security and others.
Regions: Comprises Geographical regions – North America, Europe, Asia Pacific and Rest of the World.
How it works?

Hideez Key Technology
• Authentication
• Security
• Auditability and accountability
• Ease of Use: Efficiency and Productivity
• Manageability
What is Hideez Password Manager?
• Protects against digital identity theft, phishing,• Credential stuffing, and account Take-overs
• One Key for many services
• Increased productivity of employees
• Reduced cost of operations
• Compatible with existing infrastructure
• Decreased Annual Loss
• Minimized risk of Human Error
• Business continuity
Product Diagram & Description of Product Integration
This solution sets us apart from other solutions, primarily due to the possibility of hardware storage of difficult-generated user passwords, a hard-to-select word format. Second, there is no need to have a telephone or other means of communication to confirm the user's identification in enterprises with high security requirements.
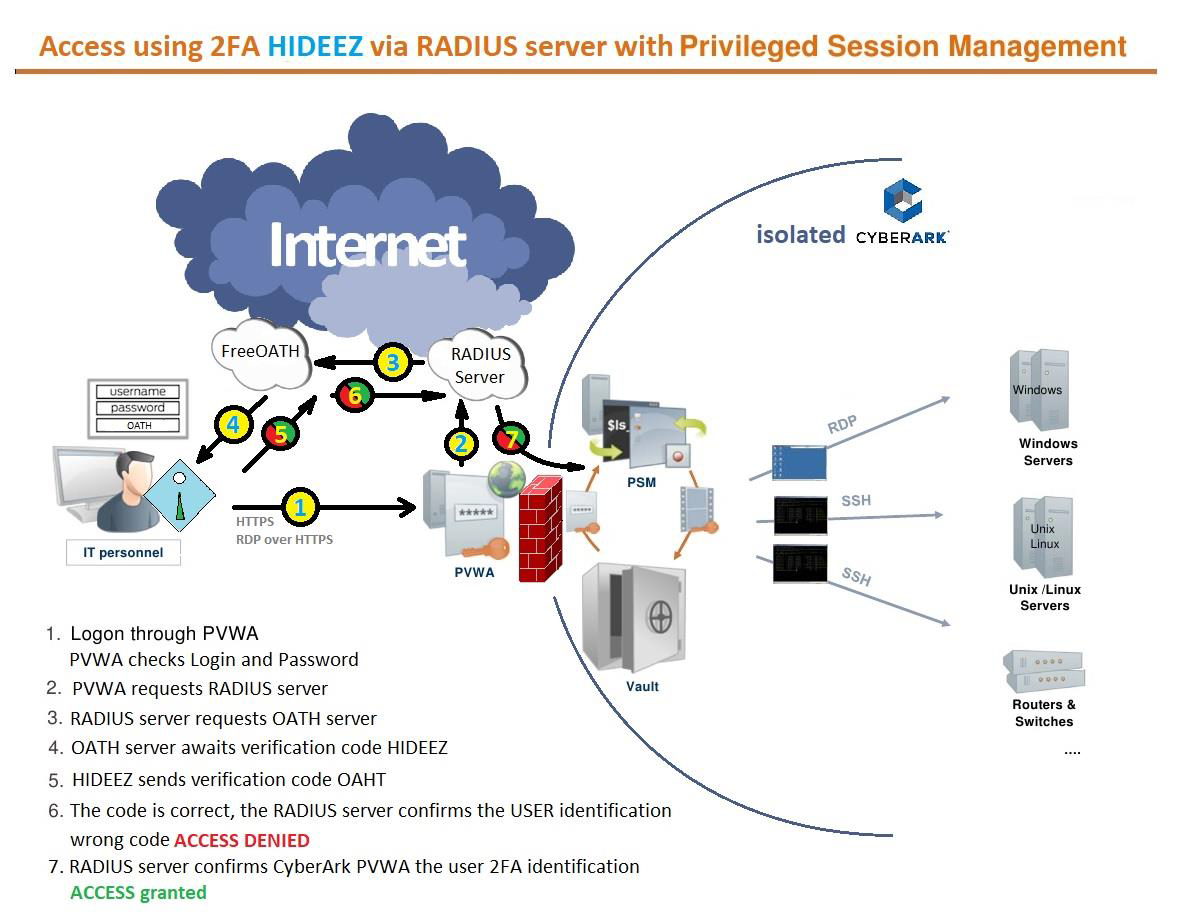
Product Installation & Integration Configuration
To deploy the Hideez Key and CyberArk interaction scheme using the RADIUS security protocol, it is suggested to use any RADIUS authentication server (for example, FreeRADIUS) installed using Ubuntu Server 18.04, with the settings of a secure channel using the CyberArk method, The Credential Provider and ASCP Implementation Guide, the Privileged Access Security Installation Guide, and the Privileged Access Security Implementation Guide. As well as bindings for the user authentication factor, the additionally raised system of multiOTP authentication or Google Authenticator. Hideez Key acts as a wireless hardware password manager, as well as an access device to the user's workplace.
Instructions for setting up and using Hideez Key (Hideez Safe) are available at
the product page or in the document repository.



