Was ist Identitätsmanagement? | Enterprise Identity Management-Lösungen
Inhalt
Identitätsmanagement für stärkere Compliance
Unternehmenslösungen für Identitätsmanagement von Hideez

Die Cybersicherheit hat in den letzten zwei Jahrzehnten enorme Fortschritte gemacht. So sehr, dass ordnungsgemäße Identitätsmanagementpraktiken zu einer Grundlage für starke Cybersicherheitssysteme geworden sind. Kurz gesagt, Sie müssen immer sicherstellen, dass jeder, der Zugang beantragt, auch tatsächlich die Person ist, für die er sich ausgibt. Ebenso wichtig ist es sicherzustellen, dass sie berechtigt sind, auf das zuzugreifen, was sie beantragen.
Mit diesem Gedanken im Hinterkopf kann die Auswahl eines bestimmten Identitätsmanagementansatzes herausfordernd sein, insbesondere wenn es um Lösungen für das Identitätsmanagement in Unternehmen geht. Um Ihnen bei der Auswahl der am besten geeigneten Identitätsmanagementrichtlinie zu helfen, werden wir in diesem umfassenden Artikel alles abdecken, was Sie zu diesem Thema wissen müssen.
Was ist Identitätsmanagement?
Identitätsmanagement (IdM), auch bekannt als Identity and Access Management (IAM), wird oft als System definiert, das von IT-Abteilungen verwendet wird, um Benutzeridentitäten und Zugriffsberechtigungen zu initiieren, zu speichern und zu verwalten. IAM umfasst zwei wichtige Prozesse: Authentifizierung und Autorisierung.
Einfach ausgedrückt beantwortet die Authentifizierung die Frage, wer Sie sind, indem sie Ihren Login und Ihr Passwort mit Ihrem Datensatz in einer Datenbank abgleicht. Die Autorisierung prüft, welchen Zugriff und welche Berechtigungen Sie haben. Das Identitäts- und Zugriffsmanagementsystem soll daher jeden unbefugten Zugriff verhindern und Alarm schlagen, wann immer ein nicht autorisierter Benutzer oder ein nicht autorisiertes Programm einen Zugriffsversuch unternimmt.
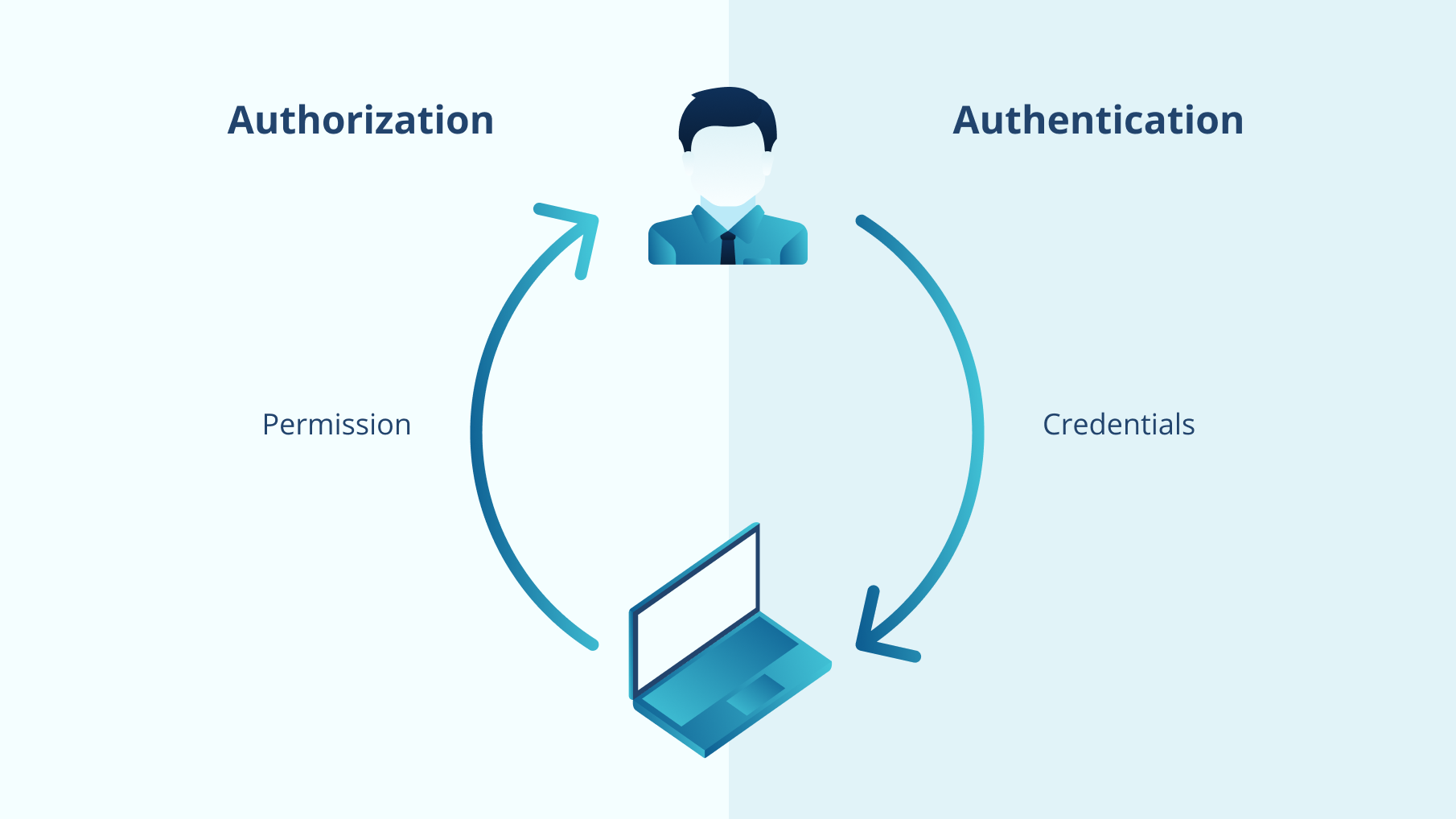
Zusätzlich ist es wichtig, Identitätsmanagement und Zugriffsmanagement zu unterscheiden. Der einfachste Weg dazu besteht darin, sich daran zu erinnern, dass das Identitätsmanagement alles darum geht, verschiedene Attribute zu verwalten, die sich auf einen Benutzer, eine Benutzergruppe oder eine andere Einheit beziehen, die Zugriff benötigt. Zugriffsmanagement hingegen bezieht sich darauf, diese Attribute zu bewerten und auf dieser Basis eine positive oder negative Zugriffsentscheidung zu treffen.
Die IAM-Methodik stellt sicher, dass Benutzer Zugang zu den Assets haben, die sie benötigen, wie Systeme, Infrastruktur, Software, Informationen, aber dass die Assets nicht von unbefugten Benutzern zugänglich sind. Der Schlüssel zur sicheren Identitätsverwaltung und Zugangskontrolle liegt in der Kombination aus starken Anmeldeinformationen, angemessenen Berechtigungen, spezifizierten Assets und dem richtigen Kontext. Identitäts- und Zugriffsmanagementsrichtlinien und -verfahren werden mit der grundlegenden Idee entwickelt, die Offenlegung sensibler Daten zu verhindern.
Konzepte des Identitäts- und Zugriffsmanagements
Identitäts- und Zugriffsmanagementlösungen wieHideez Authentication Service bestehen typischerweise aus den folgenden grundlegenden Elementen:
- einem Identitätsrepository mit personenbezogenen Daten, die vom System zur Identifizierung von Benutzern verwendet werden;
- Werkzeuge für das Lebenszyklusmanagement des Zugriffs (zur Hinzufügung, Änderung, Aktualisierung oder Löschung dieser Daten);
- einem Zugriffsregelsystem, das Sicherheitsrichtlinien und Zugriffsrechte durchsetzt;
- einem Berichts- und Überwachungssystem, das die Aktivitäten im gesamten System überwacht.
Werkzeuge für das Identitätszugriffsmanagement können automatische Bereitstellungssoftware, Passwort-Manager, Sicherheitsrichtliniendurchsetzungsanwendungen, Überwachungsanwendungen, Mehrfaktorauthentifizierung, Single Sign-On und mehr umfassen.
Mit der Entwicklung von Technologien und einer zunehmenden Anzahl von Datenverstößen reicht heute ein starkes Login und Passwort nicht mehr aus, um ein Konto zu schützen. Deshalb verwenden immer mehr IAM-Lösungen Biometrie, physische Tokens, maschinelles Lernen und künstliche Intelligenz in ihren Systemen.
Anwendungsfälle des Identitätsmanagements
Verwaltung von Benutzeridentitäten
Benutzeridentitäten werden von der IAM-Lösung verwaltet. Die IAM kann sich in bestehende Verzeichnisse für die Identitätsverwaltung integrieren, mit ihnen synchronisieren oder die einzige Quelle der Wahrheit sein. In jedem Fall wird ein Identitätsverwaltungssystem verwendet, um Benutzer zu erstellen, zu ändern und zu löschen.
Bereitstellung und Entbereitstellung von Benutzern
Eine IT-Abteilung ist für die Bereitstellung von Benutzern verantwortlich. Sie müssen neue Benutzer in das System eingeben und angeben, auf welche Apps, Software, Websites, Verzeichnisse und andere Ressourcen sie zugreifen können.
Es ist wichtig, festzulegen, welches Zugriffsniveau (Administrator, Bearbeiter, Betrachter) jeder einzelne Benutzer für jede dieser Ressourcen hat. Um den Prozess zu vereinfachen, kann die IT-Abteilung rollenbasierte Zugriffskontrolle (RBAC) verwenden. Auf diese Weise erhält ein Benutzer automatisch Zugriff, wie es durch diese Rolle definiert ist, wenn ihm eine oder mehrere Rollen zugewiesen werden.
Auch die Entbereitstellung ist ein wesentlicher Bestandteil des IAM. Wenn dies manuell erfolgt, kann dies zu verzögerten Maßnahmen und unbeabsichtigter Offenlegung führen. Der Hideez Enterprise-Server automatisiert den Prozess und deprovisioniert sofort ehemalige Mitarbeiter.
Benutzerauthentifizierung
IAM-Systeme authentifizieren einen Benutzer, wenn der Benutzer Zugang anfordert. Ein gängiger Standard ist die Verwendung von Mehrfaktorauthentifizierung, um einen stärkeren Schutz und ein besseres ID-Verwaltungssystem insgesamt zu gewährleisten.
Benutzerautorisation
Auf der Grundlage der Benutzerbereitstellung autorisiert ein IAM-System den Benutzerzugriff auf die angeforderte Ressource, wenn die Anmeldeinformationen mit den Datensätzen in der Datenbank übereinstimmen.
Berichterstattung
Um Unternehmen bei der Einhaltung von Vorschriften, der Identifizierung von Sicherheitsrisiken und der Verbesserung interner Prozesse zu unterstützen, stellt IAM Berichte und Dashboards zur Überwachung der Situation bereit.
Einmaliges Anmelden (SSO)
SSO ist eines der besten Beispiele für moderne und ausgefeilte Anwendungsfälle des Identitätsmanagements. Nur die besten IAM-Systeme wie Hideez umfassen SSO in ihrer Lösung. SSO ist eine zusätzliche Sicherheitsebene, die den Zugang für den Endbenutzer erheblich schneller macht, da es dem Benutzer ermöglicht, mehrere Ressourcen ohne zusätzliche Anmeldung zu nutzen.
Vorteile des Identitäts- und Zugriffsmanagements
Unternehmenslösungen für Identitätsmanagement bringen eine lange Liste bewährter Vorteile mit sich. Durch die Implementierung einer Zugriffskontrolle und Identitätsverwaltungslösung kann ein Unternehmen die folgenden Vorteile des Identitätsmanagements erlangen:
- Robustere Sicherheit - Ein ordnungsgemäßes Identitätsmanagement gibt Unternehmen eine größere Kontrolle über den Benutzerzugriff und reduziert das Risiko eines Datenverstoßes. IAM-Systeme können Benutzer zuverlässig anhand ihrer Zugriffsberechtigungen und Zugriffsebenen in ihren Verzeichnisprofilen authentifizieren und autorisieren.
- Schneller und einfacher Zugriff - Der Zugang erfolgt auf der Grundlage einer einzigen Auslegung der bestehenden Richtlinie. Dies ermöglicht einen einfachen Zugriff, unabhängig davon, von wo aus der Zugriff erfolgt. Das ist ein großer Fortschritt, da der physische Standort des Benutzers keine Rolle mehr spielt.
- Stärkere und effizientere interne Systeme - IAM stärkt auch die interne Richtlinienkonformität und reduziert die finanziellen, arbeitsintensiven und zeitlichen Ressourcen, die für dieses Ziel benötigt werden.
- Erhöhte Produktivität - Automatisierte IAM-Systeme steigern die Produktivität der Mitarbeiter, indem sie den Aufwand, die Zeit und das Geld reduzieren, die für die manuelle Verwaltung von IAM-Aufgaben erforderlich sind. Gleichzeitig spart dieses optimierte Unternehmensidentitätszugriffsmanagementsystem IT-Kosten, da die internen Support-Desks nicht mehr so stark frequentiert werden.
- Vereinfachte Berichterstattungs- und Prüfprozesse - IAM unterstützt Unternehmen bei der Einhaltung gesetzlicher Vorschriften, indem sie die erforderlichen Maßnahmen integrieren und auf Abruf Berichte für die Prüfung bereitstellen.
Identitätsmanagement zur Stärkung der Compliance
Da immer mehr Aufmerksamkeit und Medienberichterstattung dem Thema Datenschutz gewidmet wird, haben Regierungen und Regulierungsbehörden mehrere Gesetze und Vorschriften eingeführt, um den Schutz sensibler Benutzer- und Unternehmensdaten zu gewährleisten. Hier sind die wichtigsten, die Unternehmen für die Kontrolle des Zugriffs auf sensible Benutzerinformationen verantwortlich machen:
- PCI DSS - Der Payment Card Industry Data Security Standard ist ein weit verbreiteter Standard für Kreditkartenunternehmen. Im Kontext des Identitäts- und Zugriffsmanagements kann PCI DSS Unternehmen helfen, diesen wichtigen Finanzsektor zu regulieren.
- PSD2 - Die PSD2 ist eine Zahlungsdirektive, die große Innovationen in die Welt des Online-Banking bringt, vor allem in Form von stärkerer und besserer Authentifizierung.
- HIPAA - Dies ist eine bedeutende Identitätsmanagementrichtlinie, da sie landesweite Regeln und Standards für die Verarbeitung elektronischer Gesundheitsdaten festgelegt hat.
- DSGVO - Die Datenschutz-Grundverordnung ist seit 2018 in Kraft und ist derzeit eines der wichtigsten Gesetze, das darauf abzielt, den Datenschutz in allen EU-Mitgliedstaaten zu konsolidieren.
- CPRA - Der California Consumer Privacy Act ist das erste bedeutende Datenschutzgesetz in den USA, das sich auf die Kontrolle der Verbraucher über persönliche Daten konzentriert.
- Sarbanes-Oxley - Der SOX-Standard für Identitäts- und Zugriffsmanagementsicherheit gilt für Banken, Finanzdienstleistungen und Versicherungsunternehmen.
- Gramm-Leach-Bliley - Auch als GBLA bekannt, ist dies ein Bundesgesetz, das alle Finanzinstitute dazu verpflichtet, die Vertraulichkeit nicht öffentlicher Kundendaten aufrechtzuerhalten. Darüber hinaus verlangt es von den Institutionen, sich gegen Bedrohungen dieser Informationen zu schützen.
Identitätsmanagementlösungen können das Risiko von Verstößen gegen diese Vorschriften erheblich reduzieren. Angesichts der Kosten negativer Prüfungsergebnisse für das Unternehmen sollte die Einhaltung für jede IT-Abteilung in Unternehmen, die den oben genannten Vorschriften unterliegen, oberste Priorität haben.
Enterprise Identity Management Solutions von Hideez
Die Auswahl der richtigen Identitätsmanagementprodukte kann einen erheblichen Unterschied sowohl in der Benutzerfreundlichkeit als auch in der Sicherheit ausmachen. Bei der Hideez Group haben wir eine neue Version unseres gefeierten Enterprise-Servers eingeführt. Er ermöglicht passwortlosen Zugang mit verschiedenen Arten von FIDO-Authentifikatoren. Die Hauptkomponenten des Hideez Authentication Service sind:
- Hideez Enterprise Server - Ein FIDO/WebAuthn-Server und SAML 2.0 Identity Provider. Es handelt sich um einen sehr leistungsfähigen Server, der passwortlose FIDO2-Authentifizierung und FIDO U2F über Unternehmensanwendungen und Websites unterstützt.
- Hideez Client Software - Eine optimierte Anwendung, die die Autorisierung und Verbindung bestätigt und Hotkeys für die Eingabe von Anmeldeinformationen ermöglicht.
- Hideez Authenticator - Eine mobile Anwendung, die schnellen und sicheren Zugriff auf Unternehmensanwendungen und Webdienste mit mobiler Identifizierung bietet. Mitarbeiter können sich durch biometrische Verifizierung oder Scannen eines eindeutigen QR-Codes in ihre Konten einloggen;
- Hideez Security Keys oder andere Hardware-/Software-Authentifikatoren - Je nach Bedarf können Sie Ihre eigenen Authentifizierungstools verwenden. Wir empfehlen die Verwendung multifunktionaler Sicherheitsschlüssel, des Hideez Key 3 oder des Hideez Key 4 für maximalen Komfort und Sicherheit aller Endbenutzer, aber Sie können auch ohne sie auskommen.
Die Enterprise-Identitätsverwaltungslösung von Hideez bringt eine lange Liste von Vorteilen mit sich. Es ist eine All-in-One-Lösung, die eine einfache Passwortsteuerung ohne Offenlegung von Anmeldeinformationen ermöglicht. Sie verhindert Phishing-Angriffe und minimiert das Risiko menschlicher Fehler, was wiederum eine bessere Geschäftskontinuität ohne Unterbrechungen gewährleistet.
Wenn Sie nach zuverlässigen IAM-Unternehmenslösungen suchen und sich wirklich passwortlos anmelden möchten, erhalten Sie den Zugang zur Demo-Version des Hideez Servers völlig kostenlos, indem Sie uns sofort kontaktieren!
Oleksii Leonov ist Experte für föderierte Identitäten, Zugriffskontrolle und moderne Authentifizierungsstandards. Er ist spezialisiert auf Single Sign-On (SSO), Identitätsanbieter und Protokolle wie SAML und OIDC und hilft Unternehmen dabei, die Sicherheit zu verbessern und Authentifizierungsprozesse zu optimieren.



