What Is Proximity Login? Complete Guide to Proximity Authentication and MFA
contents

→ Download Now: Complete Guide on Physical Security Keys
Even in 2024, we still primarily rely on traditional methods of authentication based on a username/password combination. However, not only is this method impractical the more passwords you need to remember, but there are also many more efficient and more secure methods of cyber authentication.
One of the increasingly more popular forms of authentication is Proximity-Based Authentication. Utilizing a contactless login system, you get streamlined and password-free access that’s much more secure than the conventional password-based approach.
So, what is proximity login authentication, and how does it work? In this concise guide, we’ll walk you through the various proximity lock/unlock tools, the pros and cons of this authentication system, and cover all other important aspects you should know about this emerging form of authentication
What is Proximity Login?
Utilizing the user’s distance as the main factor, proximity login enables a passwordless environment that offers enhanced security with fast and smooth log-ins. A proximity login system adds a valuable layer of security and can be used as a part of a multi-factor authentication system. This can be applied when users are accessing particularly sensitive data or functionality.
In the same manner, proximity logout works on an identical principle to ensure maximum device or resource protection. Once a person is not near the device anymore, it will automatically log out until they come back near it.
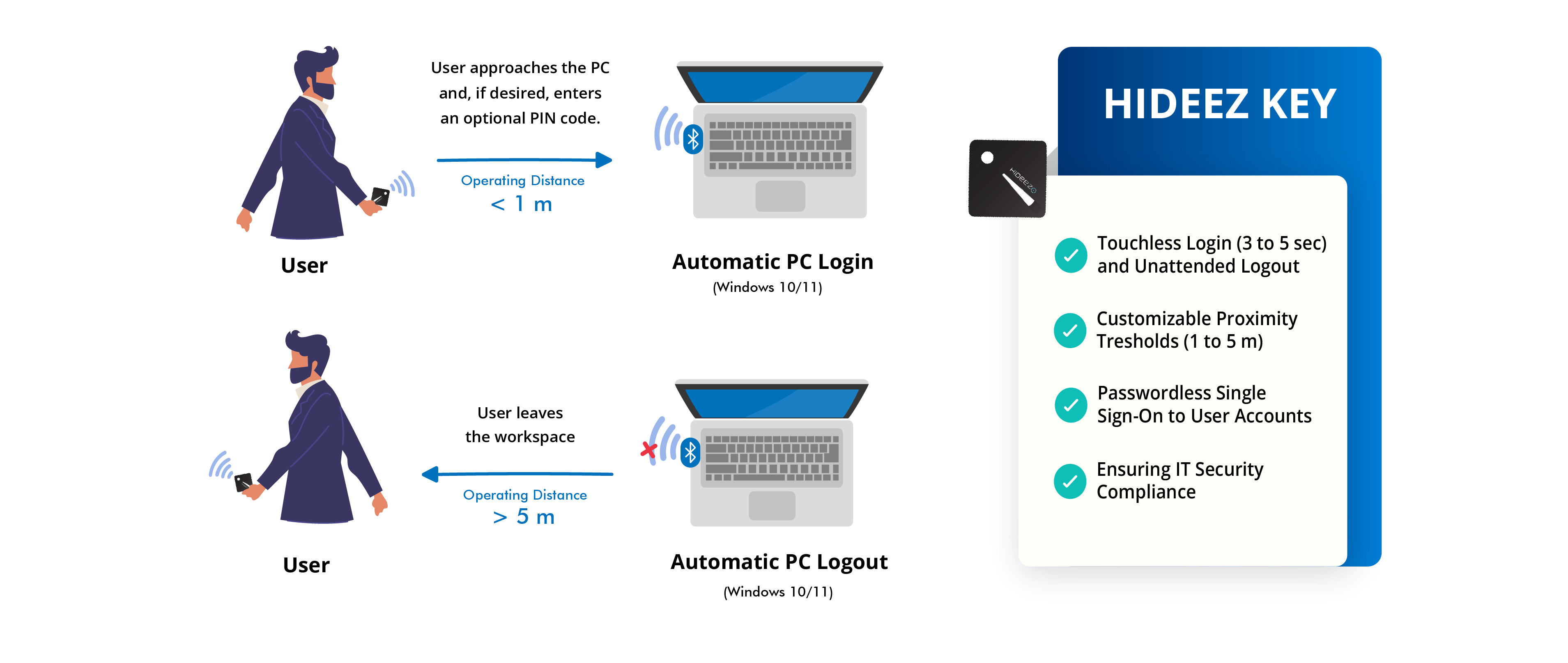
How Does It Work? - Proximity Login Tools Explained
Proximity logins are a passive mode of authentication. The user doesn’t have to do anything except be physically close to the device they want to access. That said, for this authentication system to work, besides the device you want to access, you also need a secondary device, which is a vital tool in this authentication process.
The primary device (the one you are accessing) should have sensors or detectors that would support this type of login system. Then, the secondary device, usually your smartphone or a convenient wearable like a security token or key card, indicates your proximity to the device and grants access to it.
In terms of the specific protocols, proximity authentication can work through:
BLE
Bluetooth Low Energy, or simply BLE, is a superb solution for short-range authentication. For example, an access control and door entry security system or a Windows proximity login can utilize a Bluetooth proximity login. As its name indicates, this form of Bluetooth uses less energy than regular Bluetooth. This means it can run on cheaper maintenance costs and is ideal as a proximity token for systems that don’t need to exchange a lot of data.
A BLE proximity security token can offer adjustable read ranges, making it a great solution for organizations that might need it for different applications. What’s more, using Bluetooth readers has lower set up costs compared to RFID, as there are no added costs in having to acquire objects like key fobs or RFID cards.
RFID
Short for Radio-Frequency Identification, RFID proximity authentication uses radio waves to communicate. On one side, the RFID proximity login system will have a reader that will have one or multiple antennas to receive signals.
The second component of this authentication system is the RFID tag (which can be passive or active). It stores the information that it emits through radio waves when close to the reader.
NFC
Like the previous means of authentication, Near-Field Communication uses a tag and a reader, with the latter, in this case, being a chip. In this instance, the reader chip is the active component, as it reads the information and activates the response from the tag. The tag is the passive component, receiving commands from the reader.
A common example of this are smartphone payments utilizing NFC technology. The payment terminal is the reader that sends the command, while the phone’s NFC tag receives it and sends back the appropriate information to complete the transaction.

Wi-Fi/Network Access
A Wi-Fi proximity authentication system is an excellent system for large organizations that have many employees and want to cover a massive physical area. In this system, the primary device is connected to the local area network.
When the user is present at the covered location, their device will connect to the network. This will indicate they are physically in that place and authenticate their identity.
Advantages & Disadvantages of Proximity Authentication
As with any other security system, using proximity credentials for authentication has its pros and cons. Undeniably, the most significant benefits that come from a touchless login system are speed and convenience.
- Authentication Speed. When you implement a proximity login system, you don’t have to remember passwords or PINs. Moreover, you don’t need to constantly log in and out of the devices, as everything is done automatically. This ease of use also brings added security, as you don’t have to worry whether you’ve logged out or locked your device before stepping away.
- Enhanced Security. Not only that, but such a system makes it very challenging for potential malicious actors to execute a cyberattack. Since this authentication method relies on the physical presence of the individual, it would be extremely difficult for someone to compromise this security system if they are not present in the vicinity.
- Ease of Use. This combination of speed, security, and simplicity makes it a great solution for dynamic business environments that include many workers, devices, or sites. For instance, it can be used to secure access to a building or protect desktop devices in a clinic where nurses and doctors are constantly moving between various rooms during their shifts.
Looking at the other side of the coin, there aren’t any flagrant drawbacks, as the advantages heavily outweigh the disadvantages. The main cons include setup challenges and determining the best type of proximity authentication tool you should use, which, admittedly, aren’t very concerning issues compared to the benefits.
Implementing Windows Proximity Logon & Logout
Setting up a functioning proximity computer login and logout system can boost your organization's security and productivity. If you want to implement a smooth proximity authentication solution for your organization, consider the proximity-based authentication solution by Hideez.
This service enables proximity logins using the state of the ard Hideez Keys as hardware security keys or a mobile authenticator app. It means that users can take advantage of contactless logins for Windows workstations by using biometrics or a physical factor instead of typing a Windows password.
Equally as important, Hideez Keys also have a proximity logout feature. When users leave the premises, their workstations will lock automatically. This establishes a closed security loop that safeguards your organization’s devices and resources.
You can choose between several unlock methods that best fit your authentication scenarios and security requirements. One key can be connected to any number of workstations using NFC and Bluetooth protocols. The key will also replace all your passwords with a robust passwordless SSO and MFA. Learn more or request a free pilot of our enterprise solution.
Oleg Naumenko is the CEO and founder of Hideez. He specializes in passwordless authentication, FIDO2 keys, and access management solutions. With extensive experience in information security, Oleg helps organizations transition to passwordless, phishing-resistant workforce authentication.




