Security Solutions for Manufacturing & Critical Infrastructure

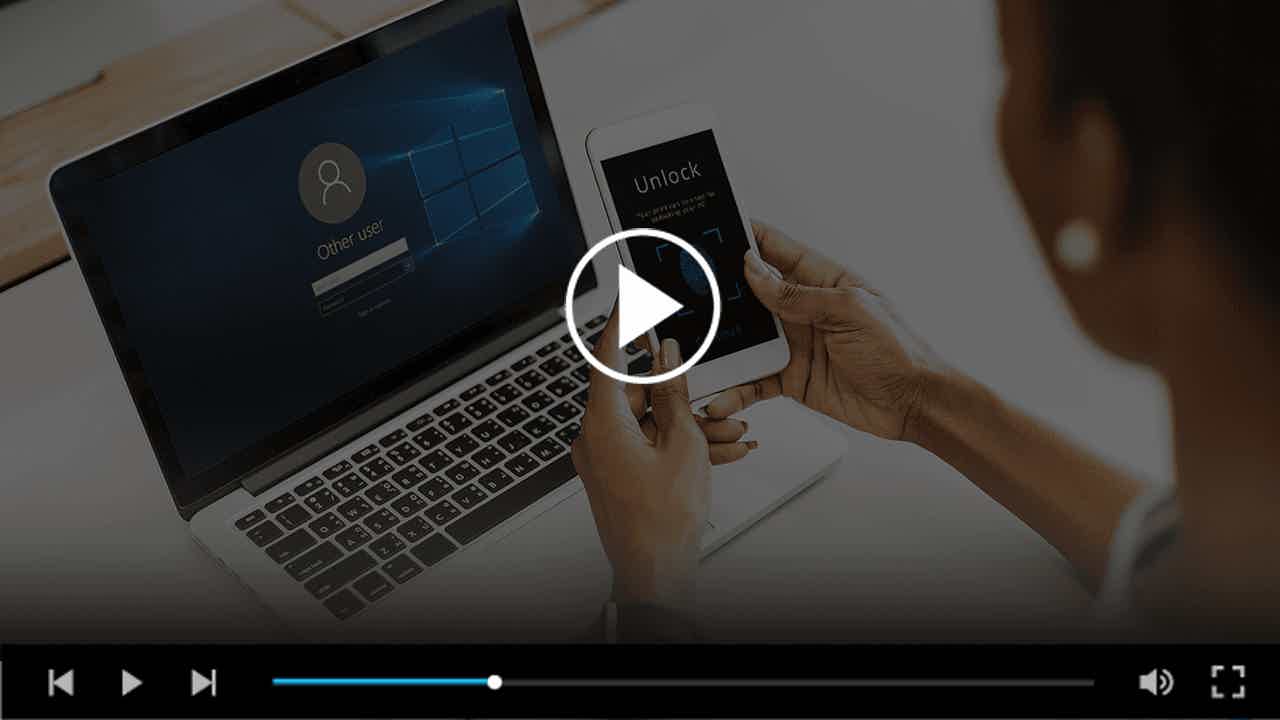
Enhance security and boost workforce productivity with the power of passwordless security solutions. Let employees access their accounts, workstations, and workspaces in seconds, minimizing the risks of data breaches.
61%
Data breaches linked to stolen credentials
105 sec.
Average time employees spend on login
73%
Average number of unmanaged OT devices
$2 Million
Expense for restoration after a cyber attack
How to ensure security at the manufacturing workplace?
How Will Your Organization Benefit From implementing passwordless Authentication and Access Control?
- Security of IT & OT Systems: By removing reliance on passwords and traditional MFA, passwordless authentication reduces the risk of unauthorized access, bolstering the overall resilience of critical industrial systems.
- Mitigation of Human Factor: By eliminating the need for manual username and password input, the vulnerabilities stemming from weak passwords, sharing practices, or susceptibility to social engineering attacks are significantly reduced.
- Seamless Access: Employees benefit from quick and hassle-free authentication, particularly crucial in environments where speed is essential. Passwordless access contributes to increased operational efficiency.
- Improved Visibility & Access Control: Advanced access control mechanisms empower administrators to efficiently manage and monitor user permissions. Access privileges align with organizational policies, reinforcing security protocols and minimizing the risk of data breaches.
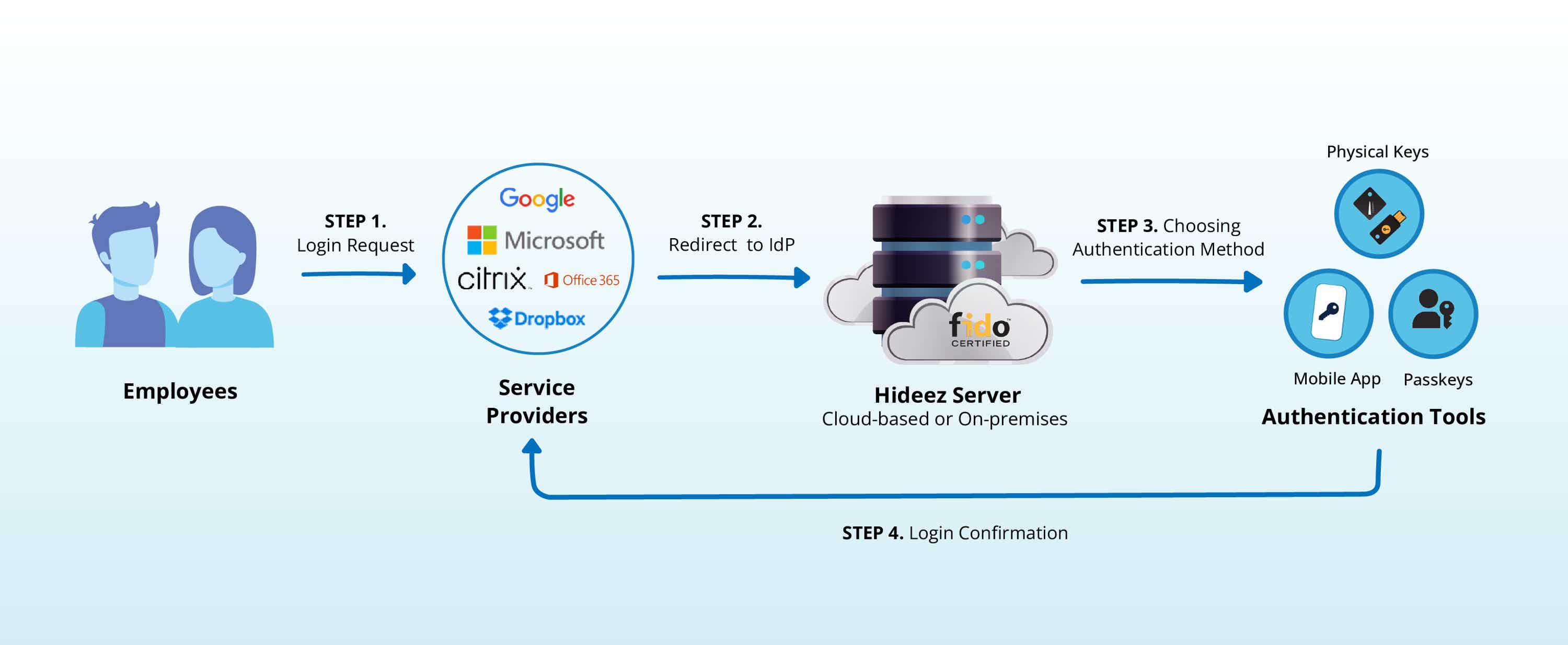
How Does Hideez Passwordless Authentication Solution Work?


Say Goodbye to Passwords: Experience True Passwordless SSO
Regardless of how many Identity Providers you have, Hideez can assist you in getting rid of passwords. By expanding your investment in SSO and making it passwordless, you can attain the highest level of assurance for all of your applications. With Hideez, the possibilities for authentication are endless!
Streamline Your Workflow with Remote Login Solutions
With Hideez, you can equip your team with speedy and straightforward passwordless security that works on all their devices, applications, networks, and more. By using Hideez, you can streamline and consolidate logins for desktops, RDP and VDI, which can boost your team's efficiency no matter where they are working from.

Proximity-based PC Login and Unattended Logout
Our hardware security vaults store up to 2,000 passwords per device. With automatic proximity lock/unlock for PCs, you can ensure that access to your desktop computers is always secure. Our solution also provides the ability for remote user logout, allowing you to end user sessions remotely.

Seamless Integration with Cloud Based and On-Prem Services
Our access and identity management tools integrate seamlessly with Active Directory and Azure AD, providing centralized authentication with SAML SSO. Our user authentication solution supports both modern and legacy applications.

Admin Console for Managing Users and Access Rights
Our user access management tools allow you to manage authentication methods and access rights of all employees, with the ability to revoke or delete users from a central admin console. With customizable solutions, easy deployment, and support, you can manage user access with ease!
Internet Connection Is Not Required for End Users
Stay connected to your corporate resources even without an internet connection. Our passwordless authentication solution allows employees to access apps and log in to workstations offline. With our mobile app, employees can using one-time access codes, while Hideez Keys offer one-touch login with a PIN code.
CASE STUDY
Hardware Security Keys
for Manufacturing & Critical Infrastructure
Explore the real-world applications of hardware security keys in an industrial setting. Discover how Hideez can improve your employees' login experience through proximity-based PC login and logout, complemented by passwordless sign-into both legacy applications and modern web services.

FIDO U2F (Level 1) Certified
FIDO2 (Level 1) Certified
Citrix-Ready Solution
Microsoft-approved
FIDO2 Security Key Vendor
Meets NIST
Password Guidelines

AWS Marketplace Product
Choose Your Package And Start Right Now!
Start delivering the seamless, secure authentication experiences your workers are looking for

Hideez Cloud
$6 per user/month (20 free users)
Multi-tenant IDaaS platform
Passwordless Single Sign-On (SSO)
Passwordless Multi-Factor Authentication
Admin dashboard for identity management
Custom Branding & Reporting
Integration: Azure AD and hundreds of popular web services through SAML and OIDC

Hideez Enterprise
$6 per user/month
Dedicated cloud service or on-premises deployment
Passwordless Single Sign-On (SSO)
Passwordless multi-factor authentication (MFA)
Admin dashboard for identity management
Smart endpoint authentication (Proximity-based login & logout)
Password-based authentication and TOTP
Remote access to servers and desktops
Integration: On-premises Active Directory, Azure AD, API, MS SQL, My SQL, SIEM