What Is IDaaS? Ultimate Guide to Identity as a Service
With the increasing number of cyber threats and data breaches, traditional methods of managing identities and access controls are becoming obsolete. Companies need a more flexible and scalable approach to handle the growing complexity of their IT environments, especially since remote work becomes more prevalent.
This is where Identity as a Service (IDaaS) comes in, offering a cloud-based solution that simplifies identity management and enhances security. IDaaS makes it easier to manage remote access, providing additional security measures to protect sensitive information while offering a seamless user experience.
What Is IDaaS?
Identity as a Service (IDaaS) is a cloud-based service that provides identity and access management (IAM) solutions. Unlike traditional on-premises IAM systems, IDaaS is delivered as a Software as a Service (SaaS) model, meaning it's hosted and maintained by a third-party provider. This approach offers scalability, flexibility, and cost-efficiency, making it an attractive option for businesses looking to modernize their IT infrastructure.
How Does IDaaS Work?
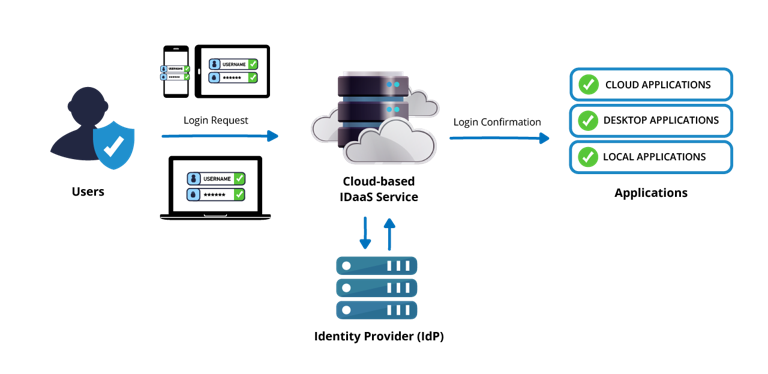
IDaaS platforms secure applications, networks, and systems via an API gateway, presenting a consistent login page for credential entry across a company’s IT infrastructure.
Upon entering credentials, the API sends an authentication request to the identity provider (IdP). The IDaaS system references a user directory containing access controls and permissions to verify the user's identity and determine their access rights. Once authenticated, the API delivers a security token to the application, detailing the user’s authorized access.
The IDaaS provider logs all interactions with the API, generating comprehensive audit and usage reports accessible via a dashboard. This ensures transparency and compliance.
Key components of IDaaS include a user directory, authentication and provisioning services, Identity Governance (IGA), and administrative tools. The user directory stores essential information such as usernames, passwords, and access permissions. Authentication and provisioning services enable secure login and resource access, while IGA and admin tools help manage user identities, roles, and permissions.
IDaaS uses industry-standard protocols and APIs, like SAML, OpenID Connect, and OAuth, to interact with applications and services. When a user attempts to access an application, a request is sent to the IDaaS platform to authenticate the user and verify their access level. Once verified, the IDaaS platform returns a token for the application to authorize user access.
IDaaS vs IAM. What Is the Difference?
Understanding the difference between IAM and IDaaS can be confusing, but it's crucial for modern IT management. Let's break it down.
IAM is the umbrella term for managing user identities and their access to resources. It includes core identity providers like directory services, which track user identities and access rights. Subcategories under IAM include directory extensions, single sign-on for web apps, and privileged access management for high-security accounts. Historically, IAM was largely on-premises and centered around tools like Microsoft’s Active Directory.
As the IT landscape evolved with the rise of web applications, traditional on-premises IAM solutions struggled to keep up. This led to the development of cloud-based solutions designed to enhance or replace these old methods, giving birth to modern IAM.
IDaaS is a subset of IAM focused on making it easier to use web applications by extending user identities with single sign-on (SSO). This means users don’t need to remember multiple logins. Initially, IDaaS solutions were added on top of traditional identity providers like Active Directory to make them compatible with web apps. However, as remote work and varied device usage became common, managing access this way became complex.
Modern IDaaS solutions now operate entirely in the cloud, providing a central platform for authenticating users and managing access to resources regardless of location or device. They enhance security by offering a single, secure identity for accessing all applications, akin to having one key for all doors.
IDaaS vs IdP
It's easy to confuse IDaaS with Identity Providers (IdPs) due to their overlapping services. However, they serve distinct functions.
Identity Providers (IdPs) manage identity information, such as user data, and provide authentication services to applications. They support functionalities like single sign-on (SSO) and automatic user provisioning. IdPs can be deployed on-premises or in the cloud, which often requires substantial setup time and resources.
Identity as a Service (IDaaS), on the other hand, offers a broader range of IAM services, including user management, security policy enforcement, audit logs, and compliance management. IDaaS solutions are inherently cloud-based, designed for quick deployment, with infrastructure and hosting managed by the provider.
While IdPs offer in-depth integrations with enterprise software and advanced provisioning, their capabilities are essentially a subset of what IDaaS offers. IDaaS aims to provide a more comprehensive, streamlined solution that integrates easily with existing applications.
Free IDaaS for SMB
Try our cloud-based identity system for workforce. Free deployment & tech support for up to 50 users.
Most Popular
June 30, 2024
Trending Articles
January 21, 2024
August 15, 2023
Trending Topics
IDaaS Types
IDaaS solutions can be classified into two broad categories: Basic and Enterprise, each catering to different organizational needs and complexities.
Basic IDaaS
Basic IDaaS is designed for small to medium-sized businesses, particularly those that are cloud-first and heavily reliant on SaaS applications. These solutions primarily offer Single Sign-On (SSO) capabilities, allowing users to access multiple cloud-based apps with a single set of credentials. This type of IDaaS is ideal for businesses without significant on-premises infrastructure, as it simplifies access management and enhances security with multi-factor authentication (MFA). User data and credentials are stored in a cloud directory, and setup wizards help administrators handle less complex administrative tasks efficiently.
Enterprise IDaaS
Enterprise IDaaS, on the other hand, is tailored for larger organizations with complex IT environments. These enterprises often use a mix of on-premises, IaaS, PaaS, and SaaS applications, requiring a more robust identity management solution. Enterprise IDaaS supports integration with existing user directories like Active Directory (AD) for authentication, and web access management (WAM) products to enforce access policies. It also provides access management for web, mobile, and API environments, bridging the gap between various systems within an enterprise's IT infrastructure. This type of IDaaS offers more granular administrative controls and customization options to meet the specific needs of large organizations.
A few examples of IDaaS Services
The IDaaS market is growing, with several vendors leading the way. While finding a one-size-fits-all platform is challenging, many standalone identity and user management solutions are available to support IAM. Here are some notable examples:
- Microsoft Entra ID (formerly Azure AD): This cloud-based service offers SSO, MFA, and directory services, integrating seamlessly with other Microsoft products.
- Hideez: Hideez provides a free platform with passwordless SSO and MFA based on FIDO2 and U2F standards. It integrates with Microsoft Entra ID, web services, and apps supporting SAML and OIDC, making it ideal for small and medium businesses.
- Okta: Okta offers a comprehensive platform with SSO, MFA, and user provisioning. Its integration capabilities make it popular among businesses of all sizes.
- Ping Identity: Known for its security and scalability, Ping Identity provides SSO, MFA, and access management, suitable for large enterprises.
- OneLogin: OneLogin focuses on ease of use and rapid deployment, offering SSO, MFA, and user provisioning, making it perfect for organizations needing quick implementation.
Good to know: For more detailed information on IDaaS vendors and their offerings, check out this list of IDaaS Solutions. This resource will help you find a provider that suits your business’s unique needs.
Why do Enterprises Need Cloud-Based Identity Management?
Enterprises increasingly rely on cloud-based identity management due to the need for scalable, flexible, and secure solutions. While traditional on-premises identity management systems struggle to keep up with the dynamic and distributed nature of modern IT environments, IDaaS leverages cloud benefits to provide centralized identity management for both SaaS and enterprise applications, supporting standards like SAML and OAuth for unified access. It also facilitates secure remote access without specialized VPNs.
IDaaS is particulartly crucial for small and midium-sized organizations needing quick, secure authentication and advanced features like adaptive authentication. It helps mitigate identity-related cyber threats, which are on the rise, and ensures compliance with regulatory standards through comprehensive logging and reporting.
Benefits of IDaaS Authentication
Enhanced Security: IDaaS authentication methods, such as MFA and SSO, significantly improve security by reducing the risk of unauthorized access. MFA adds an extra layer of protection, while SSO minimizes the number of passwords users need to manage, reducing the likelihood of password-related breaches.
Improved User Experience: By consolidating authentication processes, IDaaS simplifies user access to applications and services. SSO, in particular, streamlines the login experience, allowing users to access multiple applications with a single set of credentials.
Scalability and Flexibility: As businesses grow and their needs evolve, IDaaS solutions can easily scale to accommodate more users and integrate with additional applications. This scalability ensures that organizations can adapt their identity management practices without significant infrastructure changes.
Cost Efficiency: By leveraging cloud-based IDaaS solutions, businesses can reduce the costs associated with maintaining on-premises identity management infrastructure. This includes savings on hardware, software, and IT personnel required for system maintenance and updates.
Regulatory Compliance: IDaaS providers often include built-in compliance features that help organizations meet regulatory requirements. These features include detailed reporting, audit trails, and automated compliance checks, ensuring that businesses adhere to industry standards and regulations.
Streamlined IT Operations: Automating identity management tasks, such as user provisioning and de-provisioning, frees up IT resources to focus on more strategic initiatives. This streamlining reduces the administrative burden on IT departments and improves overall operational efficiency.
Challenges of Implementing IDaaS
While IDaaS offers numerous benefits, its implementation can pose several challenges:
Integration with Legacy Systems: Many organizations have existing legacy systems that may not easily integrate with modern IDaaS solutions. Ensuring compatibility and seamless integration can be complex and time-consuming.
Data Migration: Moving identity data from on-premises systems to the cloud involves careful planning and execution to avoid data loss and ensure continuity. This process can be resource-intensive and requires thorough testing.
User Adoption: Employees and IT staff must adapt to new tools and processes. Ensuring smooth user adoption involves training, clear communication, and support during the transition period.
Vendor Lock-In: Relying on a single IDaaS provider can lead to vendor lock-in, making it difficult to switch providers or integrate with other solutions in the future. Organizations need to carefully evaluate vendor contracts and ensure flexibility.
Security Concerns: Although IDaaS enhances security, entrusting sensitive identity data to a third-party provider raises concerns. Organizations must thoroughly vet IDaaS providers and ensure robust security measures are in place.
Navigating the landscape of IDaaS solutions can be challenging, particularly for small businesses lacking IT expertise and substantial budgets. To streamline this process and ensure you make an informed decision, take advantage of free trials offered by vendors. These trials allow you to evaluate features and understand the benefits without financial commitment.
Hideez offers a versatile range of identity solutions tailored for businesses of all sizes. Their free IDaaS platform supports up to 50 users, making it an excellent starting point for small companies looking to enhance their security and streamline identity management. By exploring these options, you can find a solution that best fits your organizational needs while saving time and resources.